In a previous article, we have seen how cybercrime is, by nature, difficult to define. However, criminologists have successfully categorized different generations of cybercriminals and constantly observe their evolution compared to technology. In this article, we’ll explore the categories of cybercrime based on criminal opportunity (modus operandi).
What is an MO?
- In criminology, MO stands for Modus Operandi, a Latin phrase meaning “mode of operating” or “method of working.” Essentialy, an MO refers to the distinct pattern or method a criminal uses to commit a crime. It’s a learned behaviour that can evolve over time as offenders gain experience and confidence, or adapt to avoid detection.
The MO involves all the actions, techniques, and choices an offender makes while committing a crime. This includes how they gain access, specific weapons, time patterns, select their victims, unusual or consistent actions during the crime, and methods for cleaning up a scene.
The MO is crucial for law enforcement because it helps link crimes, identify offenders, develop criminal profiles, and predict future crimes.
Types of cybercrime based on MO
According to criminology professor David S. Wall, online offending falls into one of three basic types of crime, each invoking a different body of law. These groups are:
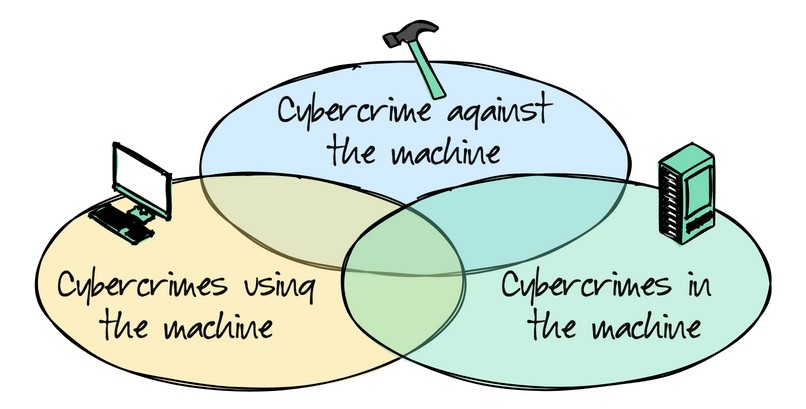
- Crimes against the machine: offending relating to the integrity to the integrity of the computer system.
- Crimes that use the machine: offending assisted by computers.
- Crimes in the machine: the offence focuses on the content of computers.
Real case scenarios often involve two or more categories, so their lines can be blurred. For example, in a phishing attack, offenders engage their victims through spam (crime against the machine), deceive them through a bogus website (crime that uses the machine), and eventually steal their information (crime in the machine).
Cybercrimes against the machine (computer integrity crimes)
- Cybercrimes against the machine (computer integrity crimes) are an unauthorized breach of computer access controls to gain access to and trespass upon networks and spaces where rights of ownership or title have already been established.
Once they get into a system, offenders move laterally across it to increase their privileges and access more remote areas where valuable information is stored. Depending on the motive, they might want to steal, destroy or block others to access it.
Crimes against the machine usually prepare the ground for a range of further crimes, either enabled by the machine or in the machine.
Cybercrimes using the machine (computer-enabled or computer-related crimes)
Crimes using machines are mainly economic crimes that involve dishonestly acquiring money, goods, or services. Most jurisdictions now have theft acts, legal procedures for recovering lost assets, and intellectual property laws to protect citizens against the illicit acquisition or the expression of ideas.
Cybercrimes in the machine (computer content crimes)
There are three main areas of crime falling in this category:
- Extreme X-rated materials and content.
- Violent materials (including hate speech).
- Extreme radical materials (terrorism).
Often, this informational content illustrates evidence of wrongdoing; sometimes, possession of it is evidence in and of itself.
The focus of criminal opportunity online
An important consideration when understanding cybercrime is who the designated victims are. What motivates offenders to target them?
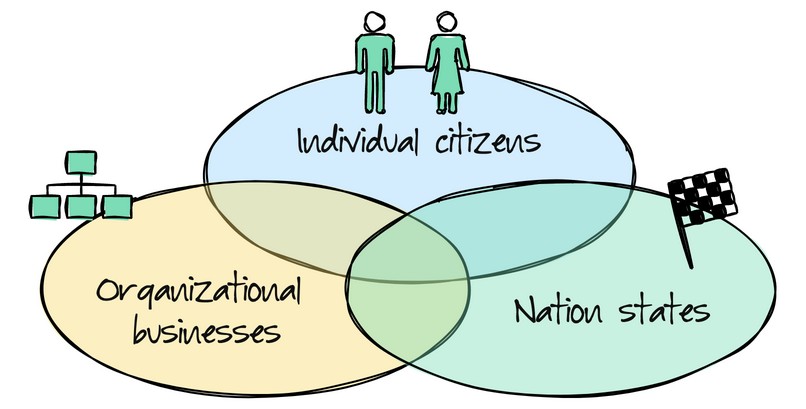
Victim groups differ in whether offenders target individual citizens, organizations and businesses, or have a bigger political picture in mind and seek to victimize nation states via their economies and infrastructures (cyberwarfare).
- Individual citizens are often affected by frauds, scams, and extortion, but also political, gender, and religious hate speech.
- Organizations and businesses tend to fall victim to larger-scale frauds, ransomware or data kidnap, which are also highly publicized by the offender to increase the victim’s reputational damage and get them to pay the attackers.
- Nation states fall victim to attacks that are tactically designed to alter the political status quo. These are usually direct attacks on infrastructure, which can inconvenience citizens and embarrass governments who may be prevented from delivering key services; or they can be more indirect such as orchestratring misinformation (fake news) campaigns, designed to change and shape citizens’ views in a particular direction. The can also nibble at businesses and economies to create a broader economic distress.
The Internet has created opportunities for old crimes and new crimes. Understanding cybercriminals’ motives, opportunities, and victims helps investigators catch them.
















