At the beginning of December 2025, some of the members of the Lazarus group were caught on camera while conducting infiltration through a fake-job scheme. But these hackers aren’t just hackers. They’re state-backed APT (Advanced Persistent Threat) group from North Korea, a full-blown criminal enterprise whose digital raids fund weapons and spread terror.
Who are Lazarus?
The Lazarus Group is widely believed to be a cyber-espionage and cyber-crime unit sponsored by the government of Democratic People’s Republic of Korea (North Korea). Over the years, the group has evolved from high-profile politically motivated hacks to large-scale financial crimes, especially involving cryptocurrencies.
Analysts consider Lazarus among the most dangerous state-linked hacker groups today, due to their sophisticated mix of cyber-espionage, financial theft, supply-chain compromise, and social engineering. The group has also global reach, targeting crypto exchanges, financial firms, blockchain infrastructure, and traditional industries. The pursue aggressive monetization using crypto theft to fund illicit revenue streams, likely supporting state ambitions and regime financing.
Evolution of their MO
Over the years, Lazarus has adapted and diversified tactics, including:
- Traditional malware, ransomware, supply-chain attacks
- Supply chain and open-source registry abuse (e.g., sneaking malicious packages into widely used repos like npm to infect developers and infrastructure)
- Phishing and social engineering, especially against developers, blockchain-related firms, or crypto-exchange employees
- “Remote-worker infiltration”: posing as legitimate IT or developer job candidates to gain access (a tactic once thought too risky for state actors, but now proven). Recent investigations have captured Lazarus operatives “live on camera” during these schemes.
This adaptability makes Lazarus not just a threat to national security but a persistent hazard to private-sector organizations worldwide.
Major recent crimes
Bybit Exchange Heist (February 2025)
In early 2025, Lazarus is attributed with a massive theft from crypto exchange Bybit: roughly 400,000 ETH (~ US$1.5 billion at the time) stolen from their cold-wallet system. This incident is widely described as the largest crypto-exchange heist to date. Security firms and blockchain analysts traced leftover funds, linking them to known Lazarus-associated wallets.
Upbit Exchange Breach (late 2025)
Lazarus is suspected of breaching South Korea’s major crypto exchange Upbit, stealing ~ 45 billion KRW (≈ US$30 million). According to local security firm data, Lazarus topped the list of APT groups responsible for incidents in the last 12 months.
These recent incidents highlight Lazarus’s shift from espionage to large-scale financial cybercrime, increasingly leveraging cryptocurrencies to monetize attacks.
The big reveal: members caught on camera
A major breakthrough occurred in late 2025, when a coordinated investigation by cybersecurity firms uncovered a long-running infiltration scheme run by Lazarus’s Famous Chollima unit.
Researchers posed as job candidates and engaged with a Lazarus recruiter offering fake “developer” contracts. The group was offered to work remotely for lucrative pay, under the promise that their “team” would handle the real work.
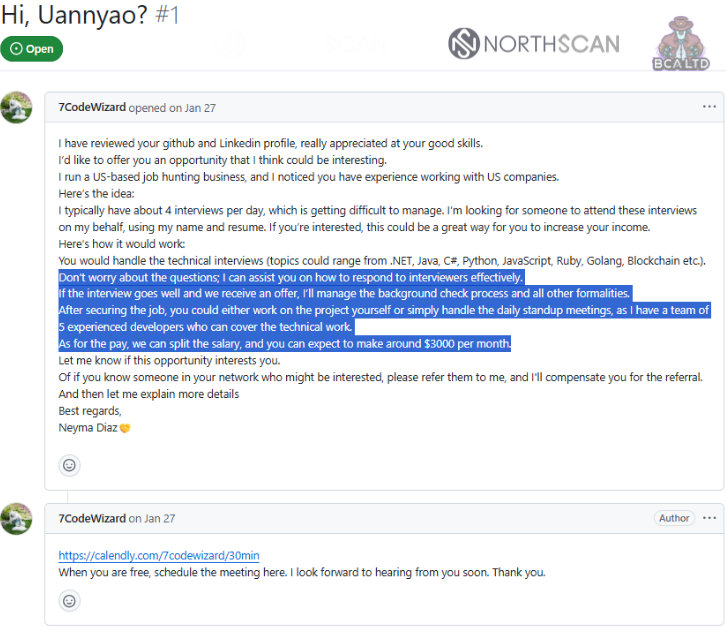
Instead of being hired, the researchers provided a sandboxed laptop, a monitored environment under their control. Once the adversaries accepted, their activity was recorded. The footage captured the hackers’ tools, techniques, operational workflow, and provided what is likely the first public, real-time visual evidence of Lazarus operators preparing an attack.
Security analysts describe this as an unprecedented window into the group’s operations.

Insights into the group
This breakthrough demonstrates that Lazarus is not only remote-only and malware-based: they now use social engineering and infiltration at the human level. This MO exposes an attack chain many organizations never considered: legitimate-looking remote-worker recruitment. This ultimately raises the bar for threat actor detection: defenders must consider identity and supply-chain trust as security vectors, not just software vulnerabilities.
What's Lazarus ultimate goal?
Cyberheists like Bybit and Upbit help finance North Korea’s regime, including weapons development and evasion of sanctions. Observers estimate Lazarus’s crypto thefts have netted billions of dollars over the past decade.
The group represents a threat to global finance and the crypto ecosystem: Lazarus hacks undermine trust in centralized exchanges and cold-wallet architecture. Their use of supply-chain and open-source registry attacks (e.g., npm) endangers blockchain software’s security (DeFi and Web3), and even institutions beyond crypto (such as banks, fintech, and traditional financial infrastructure) remain at risk.
Geopolitics meet cybercrime
Lazarus operates at the intersection of espionage, statecraft, and criminal profiteering. Their operations blur the lines between traditional intelligence, financial crime, and cyber warfare.
This means that even top-notch corporate security with full patching, hardened environments or endpoint detection may not be sufficient if identity, access management, and supply-chain trust are weak. The perimeter might be digital, but the battlefield often begins with the human trust chain.
















